Some Notes Re: SharePoint 2010 User Profile Synch Service
So there’s a lot been said about the User Profile Synchronization Server in SharePoint 2010.
Let’s take a minute to point out a couple of interesting points.
First, returning as our new best friend in Harbar his Rational Guide to the UPSS. So we’re not going to try to improve upon or replace any of that except as follows.
Once we’ve deployed our two server farm in a friendly domain, we’re going to run the Configuration Wizard in Central Admin. Now that will do a lot of things but it won’t get the UPSS running.
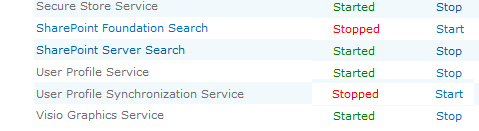
So we visit Services on Server and we’ll see:
So, we click Start and it changes to Starting for a minute but then you refresh and it’s gone back to Stopped.
Also, we go to the Manage Service Applications, which is different from Service on Server, by selecting Application Management | Manage Service Applications and clicking on the User Profile Service link:
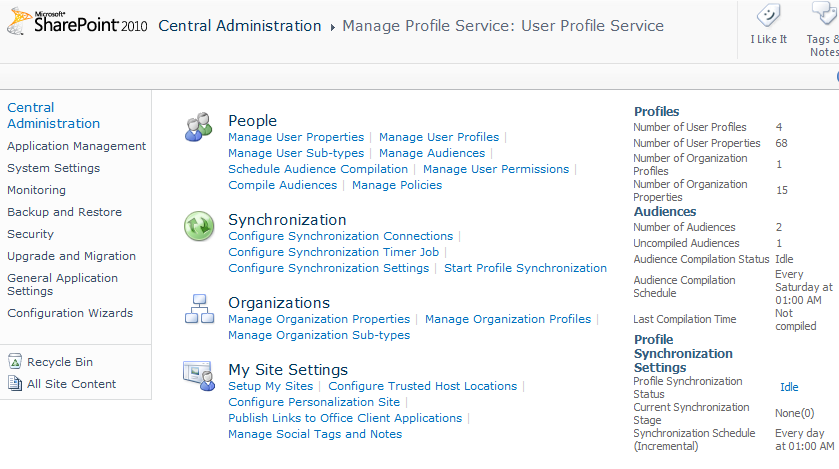
… where we find the <hidden> Manage Profile Service: User Profile Service page:
Here, we try to Configure Synchronization Connection and Create New Connection and SharePoint barfs saying it can’t load the page because the profile service is running or not running or something.
So here’s what’s happened. When we ran CA’s configuration wizard, it tried but failed to initiate the UPSS and left it hung and it hung for a couple of reasons and left some splat files in various places that we have to fix.
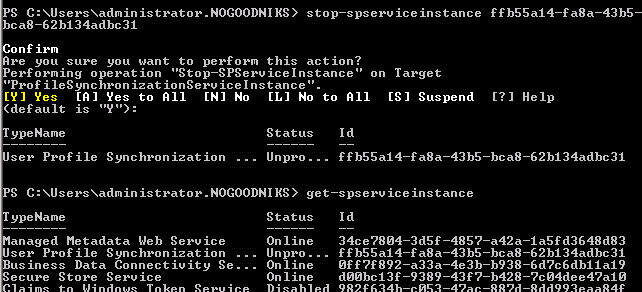
First, we have to stop the service that’s trying it’s best to run. This is a SharePoint Management Shell (i.e. PowerShell) task.
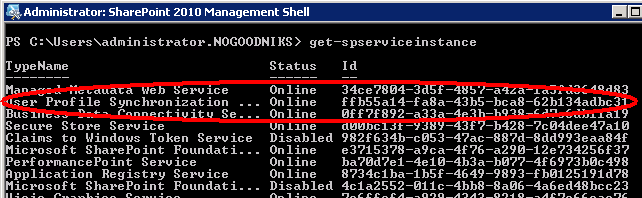
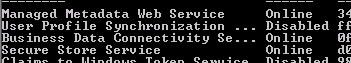
We run Get-SPService and see that the service is, in fact, online:
We get the GUID and run Stop-SPService Instance <GUID>
… and it takes a moment to “Unprovision” itself.
Then, it’s Disabled.
Now we can do a couple of things.
First, we can go delete the certificates it created with that bad GUID by running MMC and loading the Certificates Snap-in. Now, we’ll have to do this for the local computer and for the logged-in user, but we drill down to all the certificate stores and everywhere we find a ForeFront certificate, we’ll delete it.
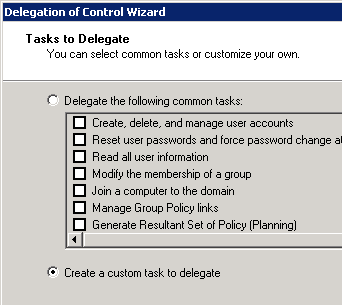
Then we’ll go into Active Directory and right-click on our domain and select Delegate Control. Here we run through the wizard, select our service account and then select the Create a Custom Task option:
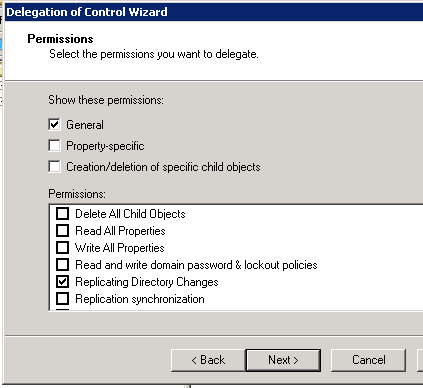
… Then, on the Permissions page, I check the Replicate Directory Changes permission:
Then finish the wizard.
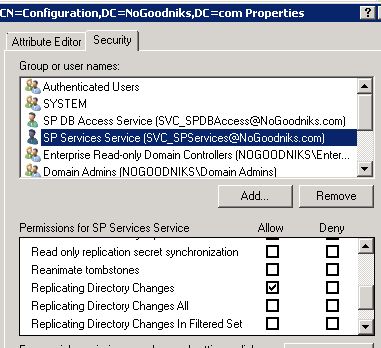
Lastly we run ADSIEdit.msc on the domain controller. Here, we’ll connect the root to a Well Know Naming Context called Configuration. Then, we’ll right-click on the configuration and select Properties.
On the Security tab, we’ll add our service account and give it the Replicating Directory Changes permission:
Then we’re done with that, we can start our UPSS and create our connection.
hth
-robot